Dell Wyse ThinOS – For High Level Security
Endpoint Security
You may still remember a sort of ransomware the WannaCry created a sensation globally. After that many companies start considering how they should protect their end-points again.
According to one research, 95% of security infringements in corporation rise from an end-point. In addition to anti-spoofing by vein recognition solution provided by mofiria, it is important to enhance the security of end-point itself. Even if you manage your confidential information centrally in your data center by constructing VDI system, an end-point can be a security hall when it is attacked.
Since acquired Wyse Technology that was a well-established thin client vendor in 2012, Dell is contributing in introduction of secured VDI environment into corporations as a leading company for thin client solution.
One of the major features for Dell Wyse is the operating system ‘Dell Wyse ThinOS’ developed specialized for VDI.
It doesn’t have a public APIs unlike Windows or Linux nor application like a browser or mail client that can be a intrusion route for malware. This feature enables ThinOS to be unrelated with any attacks.
Influences of Past Security Problems to Wyse ThinOS
As you can see the table below, The influences any past critical security problems affected to ThinOS has been very small proves its high security level.
| Problem | Reported when | Overview | Influences to Wyse ThinOS |
| LPD vulnerability | August 2001 | Due to buffer overflow vulnerability on print server program (LPD), a third parties can do any operations with administrator rights. | No influence since LPD service is invalid by default. |
| POODLE | October 2014 | Due to the vulnerability of SSL3.0 and TLS1.0/1.1, a third party can intervene in communicating to a server that enables them. | Though it supported SSLv3 those days, no infulence unless the old SSLv3 was enabled on server side. Now it doesn’t support the SSLv3. |
| Bash Shellshock | September 2014 | Due to the vulnerability of Bash, a third party can execute any code or program. | No influence since ThinOS doesn’t include Bash. |
| WannaCry | March 2017 | A third party can execute a code remotely by making use of the vulnerability of SMBv1 for Windows (MS17-010). | No influence since ThinOS doesn’t include SMB. |
In addition, Dell carries out a penetration test by third party organizations periodically and launches the products after verifying thoroughly possible security risks in ThinOS.
That’s why Dell keeps such high level security.
Features of Dell Wyse ThinOS
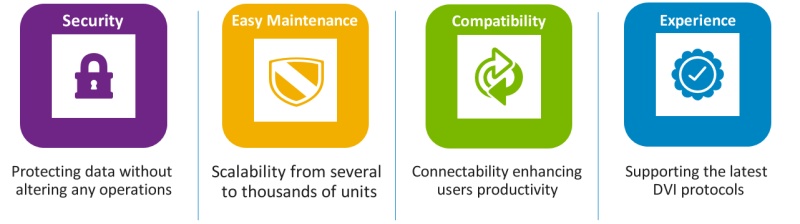
Compatibility with mofiria vein authentication
The latest version of Dell Wyse ThinOS version 8.4 has been confirmed working with mofiria vein authentication devices with all sorts of connection protocols.
We provide you with the VDI with high security level with confidence by the combination of:
anti-spoofing by two-factor authentication using mofiria’s vein authentication device
strong end-point by Dell Wyse ThinOS
Related page:
Desktop Virtualization and Cloud Client-Computing
Author of this article

| Dell Inc. Cloud Client-Computing Division |