Solution Deployment Utilizing Bluetooth Connected Vein Authentication

— Building accurate security environments using Bluetooth connected vein authentication unit, FVA-U4BT — Working Together with Attendance Management System idearecord, inc. has a concept as ‘Web solutions on chain store business’ and helps the customers to solute various problems around chain stores.idearecord’s cloud type attendance management system ‘CREW CHECKER’ enables identity verification using mofiria’s Bluetooth connected finger vein authentication unit FVA-U4BT.It helps to remove common problems regarding time card and ID card such as forgetting to punch, losing a card and unfair processing including proxy time recording. Since each finger has a different vein pattern, it is so hard to forge and impersonate. Thus, finger vein authentication is very effective […]
Logon Software for Mac and Windows – @SECURE/fv
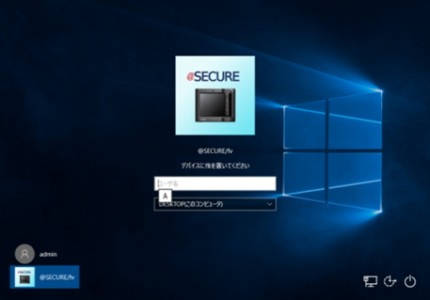
Enlarging Scope for Using Mac Computer Recently more corporations and organizations start using Mac computers for their operations.In an interview of a company president on television, we often see a laptop Mac computer placed on the desk.Before, as most business application system ran on Windows computer only, we didn’t have an alternative choice. Due to recent system transitions to cloud computing, you can access business application system from anywhere using a web browser. Thus, you don’t necessarily need to have a Windows computer and accessing to the system from outside of the office via internet connection is getting popular. However, in terms of protecting personal information and/or corporate confidential information, […]
Visiting Our Partner – 01 Systems WLL

The other day I visited one of our most important business partners in Middle East, 01 Systems WLL. This article is the report of my visit and the introduction of this innovative company. 01 Systems has its headquarter in Manama, Kingdom of Bahrain and the branch offices in other Middle East countries and India. They are implementing their solution services globally including mainly Middle East and North Africa. One of their representative solutions is content management system by the combination of signatory management and biometric authentication. They provide it depending on the customers demands.They are utilizing mofiria’s finger vein authentication technology into the system used for identity verification at bank’s […]
Dell Wyse ThinOS – For High Level Security

A new article has been posted on Biometrics and Security Blog.The title is ‘Dell Wyse ThinOS – For High Level Security‘.This article is a guest post by Dell Inc.
Introducing Cloud-based Vein Authentication Solution (Security Solution from T4U Part 2)

※This article is a guest post by T4U Co.,Ltd Part.1: Security Circumstances and Multi-Layered Protection (Security Solution from T4U Part 1) Cloud-based Vein Authentication Solution – VIP System The VIP System is a security solution based on multi-layered protection. VIP is stand for Vein Identification Platform.It is a combination of thin client system and finger vein authentication enabling realtime monitoring and data encryption. In thin client system, a terminal doesn’t have information and using external device can be prohibited. Therefore, it can keep high security even if the user is not familiar with IT related knowledge.Thin client system provided by T4U can protect not only the endpoint but also any data […]
Security Circumstances and Multi-Layered Protection (Security Solution from T4U Part 1)

※This article is a guest post by T4U Co.,Ltd In general, we regard ‘Security’ as a kind of obstacle that prohibits various things or makes anything inconvenient. The security solution T4U proposes enables the users to build an environment that they can concentrate on their own business. In addition to being safe, the users can spend their time in their proper work instead of managing passwords and rules. Security incidents in Japan The following table and chart were reported by Japan Network Security Association on May 2017 and these elements show security incidents occurred in 2016 and those causes.As you can see, the total number of persons whose info was […]
Introducing EVE MA – Multifactor Authentication Integrated Platform

※This article is a guest post by DDS, Inc. Features of EVE MA EVE MA is a high expansibility plugin architecture, which enables a flexible configuration on authentication base for enterprise system.It replaces the method of user authentication for various systems from ID and password entry to multi-factor authentication method using different biometric modalities (fingerprint, mofiria’s finger vein, palm vein and face recognition), IC card (FeliCa and MIFARE) and so on.Assured identity verification reduces any security threats. It cooperates with Active Directory seamlessly and enables a flexible configuration for any organizations and groups. EVE MA integrates multiple authentications such as Windows Logon, business applications and virtual desktop, and provides safe […]